InfectoMeter: A Tool that Helps to Place Bug Fixes
InfectoMeter measures the infection impact of each source code line of a Java program, given a failed unit test run. It visualizes the impact by coloring the code. The darker the color, the higher the impact of that line of code on the rest of the execution.
Note that the coloring does not indicate the points where the bug might have occurred. It indicates the size of the impact a line has on the rest of the execution, no matter whether that line was buggy or not. InfectorMeter is implemented on top of BLAST. The following image shows a sample output of InfectoMeter for a Demo program.
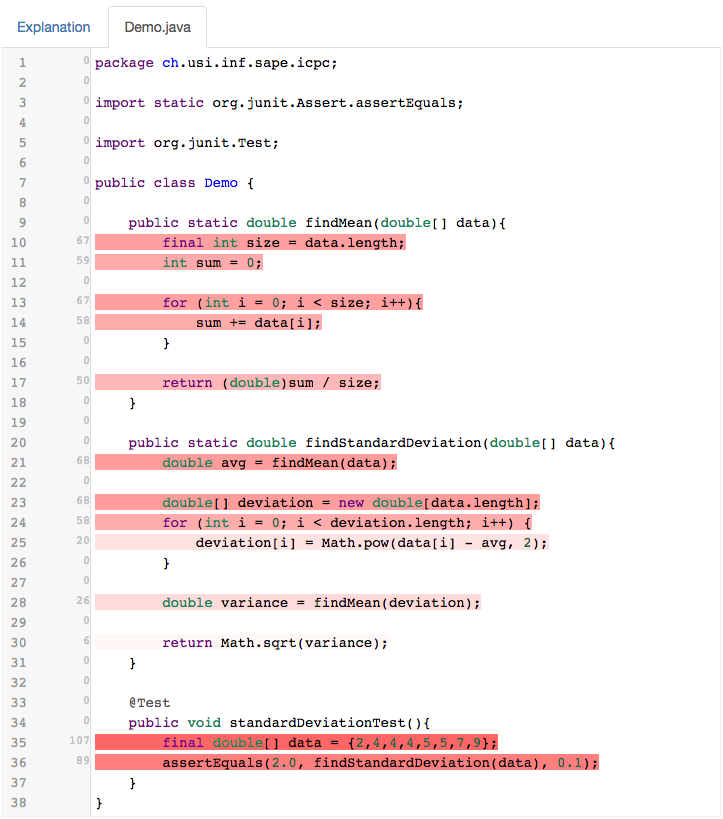
InfectoMeter Backend
InfectoMeter consists of a backend and a frontend. The backend is built on top of the BLAST information-flow tracing framework.
Get InfectoMeter Backend Source Code
You can download infectometer.zip which contains the source code of the InfectoMeter backend.
Build InfectoMeter Backend
Given that InfectoMeter is implemented on top of BLAST, the build process is equivalent to the build process for BLAST, i.e.,
- Import the Eclipse project into an Eclipse IDE and build it through running the build project under the Project menu
- Use Ant with the build.xml to build the agent. For this, you need to use the ant target "make-agent-jar"
Launch InfectoMeter Backend for a Unit Test
InfectoMeter is designed to start the analysis from the predicate defined in a unit test. So, the input program which is to be analyzed should be wrapped as a JUnit test. To launch InfectoMeter, a special target called "infecto" is defined in the ant build file. Within this target action, there are four switches that need to be set by the programmer to customize the tool for the to-be-analyzed program:
- -Dapp: This indicates the base address of the program to be analyzed. All classpath addresses are computed relative to this address.
- -Dcp: The classpath address of the program relative to the base address of the program. It can be a set of addresses.
- -Dtc: The fully qualified name of the class which contains the unit test. The class should locate under the classpath.
- -Dtm: The name of the test method.
Once launched with appropriate information, it runs the test with full dynamic information-flow tracking within the execution and then it generates a set of JSON files corresponding to each source file used in the test. Each JSON file contains the information about the raw value of impact as well as its normalized value for each line in the source code. The JSON files will reside in a directory called "infecto" under the base application address specified by the programmer.
InfectoMeter Frontend
To visualize the results, we provide a simple front-end implemented as single-page web application.
Get InfectoMeter Frontend Source Code
You can get the git repository with the source distribution for the visualization front-end.
Launch InfectoMeter Frontend
Because the Javascript code in this application needs to access various files, the application does not work when opened via a file: URL. The application only works if it is served from some web server. The easiest is to cd into the directory that contains the files of this web application, and to run the simple HTTP server included in Python:
python -m SimpleHTTPServer
and to open the page using http://localhost:8000/infectometer.html. Before opening the page, copy all of the analyzed java source files and the corresponding generated json files into the same folder where the front-end is located.
You can specify which file(s) to visualize multiple files by providing them as query string parameters in the URL, e.g., http://localhost:8000//infectometer.html?file=Hello.java&file=World.java visualizes the two files "Hello.java" and "World.java" with their respective infection impacts.


